Federal Certification
Get expert support for the rigorous and high-scrutiny federal frameworks, including FedRAMP (NIST 800-53r4), CMMC (NIST SP 800-171), CCPA, FFIEC, NYDFS, CJIS, DoD RMF, and FISMA.
End to End-managed Federal Compliance and Certification
Leveraging our proven expertise gained from providing federal certification advisory services to more than 4,000 organizations, we help you plan and execute a seamless journey tailored to your requirements. Our approach is built on years of experience supporting organizations of all types as they pursue the FedRAMP and DoD marketplace.
E Secure 360’s comprehensive federal portfolio, including FedRAMP (NIST 800-53r4), CMMC (NIST SP 800-171), CCPA, FFIEC, NYDFS, CJIS, DoD RMF, and FISMA, is backed by the industry’s most tenured audit and advisory team. It spans business case development to ongoing management.


E Secure 360’s approach
Our approach to helping you achieve and maintain certification comprises three activities: gap analysis, readiness preparation, and documentation development. Our FFIEC Certification methodology provides financial institutions with a framework that helps them measure their inherent risk profile and their information security maturity.
In-depth information-gathering session with stakeholders to learn about organizational structure, information systems, control implementation status, overall compliance posture, and any other concerns regarding position
Data analysis to understand the implementation status of each security control and appropriately identify control deficiencies
Cyber incident management and resilience
Customer Awareness and Education
Federal Assessments
Comprehensive Federal Compliance portfolio – which is backed by the industry’s most tenured audit and advisory team – spans business case development to ongoing management.
FedRAMP
Federal Risk and Authorization Management Program (FedRAMP) (NIST 800-53r4)
FedRAMP assessments from the most experienced 3PAO in the industry.
CMMC
Cybersecurity Maturity Model Certification (CMMC) (NIST SP 800-171)
Effectively plan and prepare for CMMC with help from our CMMC advisory and assessment services.
CCPA
California Consumer Privacy Act (CCPA) Compliance
Ensure you protect consumer data and meet security requirements outlined in the California Consumer Privacy Act.
DoD RMF
Department of Defense Risk Management Framework (DoD RMF) Compliance
Establish the cybersecurity Risk Management Framework (RMF) for DoD Systems and provide guidance on reciprocity of system authorization decisions for the DoD in coordination with other Federal agencies.
FFIEC
Federal Financial Institutions Examination Council (FFIEC) Compliance
Aligned with the FFIEC examiner audit protocol to help financial institutions safeguard customers’ and members’ personal financial information. Learn More >>
NYDFS
New York Department Of Financial Services Cybersecurity Regulation (NYDFS) Compliance
The NYDFS Cybersecurity regulation is designed to protect consumers and to “ensure the safety and soundness of the institution,” as well as New York State’s financial services industry.
CJIS
Criminal Justice Information Services (CJIS) Security Policy Compliance
The CJIS Security Policy integrates presidential directives, federal laws, FBI directives and the criminal justice community’s APB decisions along with nationally recognized guidance from the National Institute of Standards and Technology.FISMA
Federal Information Security Management Act (FISMA) Compliance
FISMA is federal legislation that defines a framework of guidelines and security standards to protect government information and operations.How can we help?
Our approach to helping you navigate the journey to Federal certifications comprises three activity groups: readiness, initial, and annual assessment.
Address the NIST requirements.
E Secure 360’s combined NIST Advisory and Cyber Engineering teams have developed a process to enable cloud service providers to be audit-ready in less than six weeks and at a fraction of historical costs. We view all companies as being on a journey to appropriately understand and address their cyber risk. The journey has three phases:
- Understanding risk – Companies assess what cyber risk means for them, identifying the critical assets that drive the business and the nature of
the threats they face. - Prioritizing risk – Companies focus more precisely on the areas that matter most and make decisions based on those priorities.
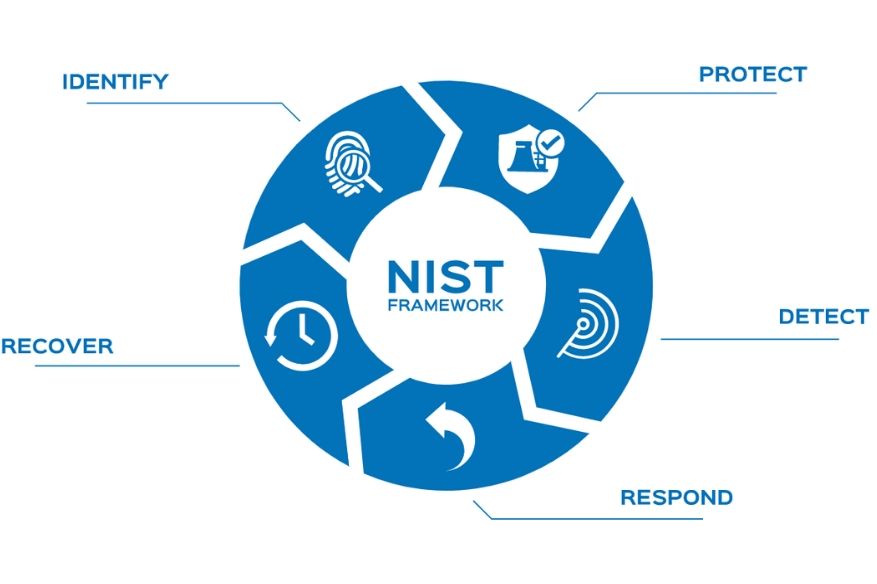
- Monitoring risk – Companies develop the ability to know with increasing agility when changes in the technology or business environment or evolving threats change their risk exposure. For example, they may have implemented advanced capabilities for monitoring technology assets and deploying automated threat response. In other words, the five CSF functions—Identify, Protect, Detect, Respond and Recover—operate in harmony.
Unparalleled cybersecurity compliance experts
For more than 20 years, we’ve been at the forefront of compliance with the ability to coordinate and streamline the broadest set of compliance requirements in the industry.
- Our comprehensive Federal portfolio – which is backed by the industry’s most tenured audit and advisory team – spans business case development to ongoing management.
- Our teams are highly experienced and well versed in NIST 800-53 and DoD requirements and how they relate to commercial cloud environments.
- Our dedicated team of specialists ensures we provide the best guidance to handle the most complex scenarios.
- We work with the industry’s largest cloud service providers (e.g., Google, Amazon, IBM, Microsoft), and 75% of our engagements are facilitated for cloud service providers (e.g., SaaS, IaaS, PaaS).