Network Penetration Testing
Our Network penetration testing service helps to Identify ways to exploit vulnerabilities or to circumvent the security features of system components and provide remediation support
Evaluate Your Security Stance, Think Like an Attacker
The most accurate method to evaluate your organization’s information security stance is to observe how it stands up against an attack. Our experts perform a simulated attack on your network to identify faults in your system, but with care to help ensure that your network stays online.
We follow a structured methodology to ensure a thorough test of your entire environment and meet regulatory requirements as PCI DSS, GLBA, HIPAA, SOX, EU GDPR, ISO 27001, FISMA/NIST.

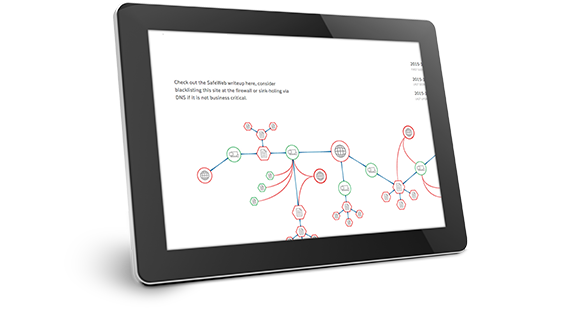
Comprehensive Reporting with remediation tracker support
Comprehensive reporting with Executive Summary and detailed vulnerability analysis, recommendations with prioritized action plan. Video and Image evidences are presented with the network penetration testing report that show cases the live demonstration of exploiting the vulnerability which will help the technical teams to understand and fix the vulnerable finding faster and effectively.
The network penetration test report address the Regulatory requirements including PCI DSS, HIPAA, SOX, FISMA and GLBA.







