SOC 2 Report and Certification
As an independent third-party service auditor, we can help companies prepare for SOC 2 report attestation, including identification of key areas necessary for compliance, perform control testing and sign the audit opinion accordingly
American Institute of Certified Public Accountants (AICPA) Membership
E Secure 360 Certified Public Accountants (CPA) panel holds membership from AICPA and is authorized to attest the SOC 1, SOC 2, and SOC 3 reports
END-END SOC 2 COMPLIANCE MANAGEMENT
Implementation, Remediation Guidance, Audit and Certification
Businesses are increasingly reliant on third-party suppliers to deliver business-critical services related to information technology (IT), including managed IT services, software as a service (SaaS), and security as a service. We work closely with our clients to proactively
- Identify value-added business insights, provide suggestions for improvements throughout the engagement,
- Prepare for SOC 2 report attestation, including the identification of key areas necessary for compliance with SOC 2’s methodological
requirements, as well as other industry standards; - Perform control testing in line with the applicable standard and sign the audit opinion accordingly.
TRUSTED COMPLIANCE PARTNER
Recognized as a Leader in Cyber Security and Compliance Management
We build your capabilities to manage risks with actionable insights and address regulatory requirements
PRAGMATIC APPROACH
Structured SOC 2 reporting for Managed and Cloud Service providers
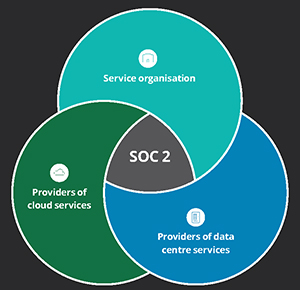
Our SOC 2 Audit approach utilises the American Institute of Certified Public Accountants (AICPA) standards to provide an audit opinion on the security, availability, processing integrity, confidentiality and/ or privacy of a service organisation’s controls.
Considering the broad spectrum of services, we follow a pragmatic approach that is customized to meet the specific business needs of our clients that provide cloud computing (i.e. software-as-a-service, infrastructure-as-a-service, platform-as-a-service), Blockchain, Technical services, Managed services, and Staffiing solutions with a risk-centric focus.
SOC 2 REPORTING OPTIONS
SOC 2 Type 1 and SOC 2 Type 2 Options
We can support both SOC 2 Type 1 and SOC 2 Type 2 report options that are either as a point in time assessment or an assessment of design and operating effectiveness over a period of time.
The E Secure 360 performance assurance team is well versed in assisting outsourced service providers and their customers with understanding the SOC reporting options and can assist organizations through the multi-stage process to issue a SOC 2 Type 2 report. Our SOC 2 approach and reporting can help reinforce stakeholder confidence and can be applied for regulatory or non-regulatory purposes to cover business areas outside of financial reporting.

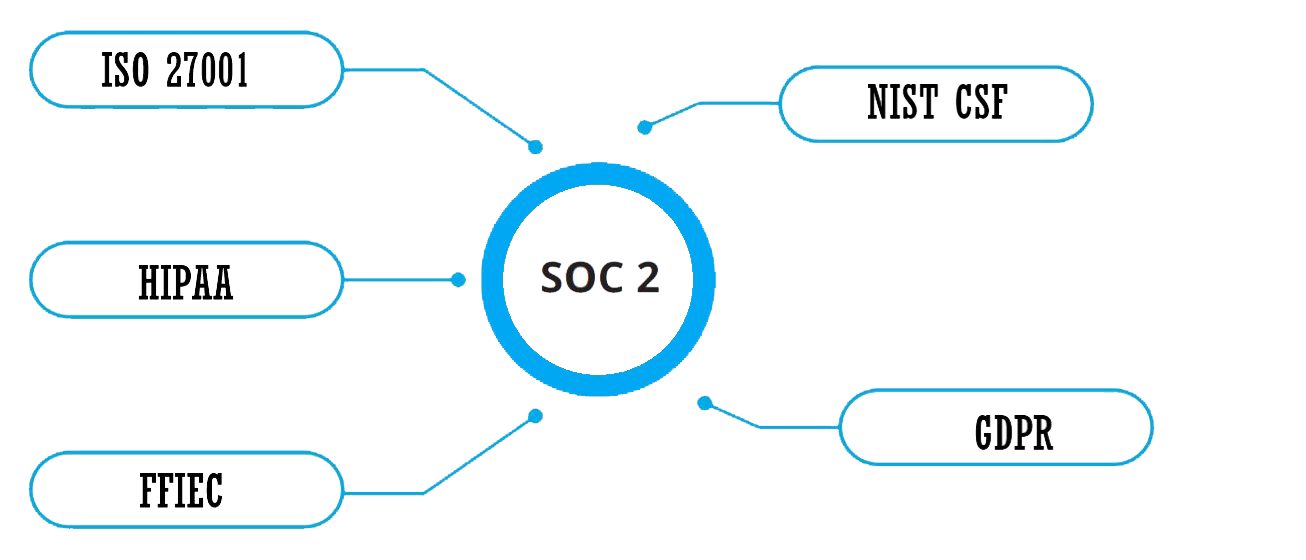
EXTEND SOC 2 COMPLIANCE
Add-on options to undergo a single SOC 2 audit and comply with multiple standards
Today’s regulated industry requires Organizations to comply with multiple regulations and standards. E Secure 360 follows a pragmatic approach for SOC 2 compliance and certification leveraging GRC framework that can enable organizations to extend the SOC 2 compliance program and enable to get certified with standards of ISO 27001, GDPR, NIST CSF, and HIPAA.
INNOVATE WITH CONFIDENCE
The data shows why E Secure 360 is the right partner for your security and compliance strategy
RELATED ARTICLES
Resources to help you drive compliance and speed within your enterprise
Get compliant with PCI, HIPAA, GDPR, FedRAMP, SOC 2 by cloud services of AWS, GCP and Azure
This article provides guidance on how to get your business compliant with PCI, HIPAA, GDPR, FedRAMP, SOC 2 by leveraging cloud services of AWS, GCP and Azure. Organizations providing IT Managed Services, Software Development, Software [...]
SOC 2 Audit Controls and Checklist
The AICPA Assurance Services Executive Committee (ASEC) has developed a set of criteria (trust services criteria) to be used when evaluating the suitability of the design and operating effectiveness of controls relevant to the [...]
Illustrative Examples for SOC 2 certification
Is your client information and data safe? How will you assure it? Two very important questions for which you should have very clear answers if you offer IT services to your clients. If you are an [...]
The cost of SOC 2 Certification services
Today, more than ever, organizations need to ensure the security, availability, privacy, processing integrity and confidentiality of their data and underlying systems—regardless of whether they managed are in-house or outsourced. E Secure 360's Information & [...]
WHY WORK WITH US?
Recognized as a Leader in Cyber Security and Compliance Management
E Secure 360 has the depth and breadth to deliver leading practices on SOC 2 matters. We tailor our service to your needs, reducing the effort needed to gather the required information while helping you and your staff gain a clearer understanding of the SOC 2 requirements.
- Certification granted by the acknowledged industry leader
Global team of risk advisory and privacy specialists
Thought-leaders with involvement in associations such as ISACA and AICPA
Unique approach and experience in startup SOC 1, 2 and 3 audit situations